Description
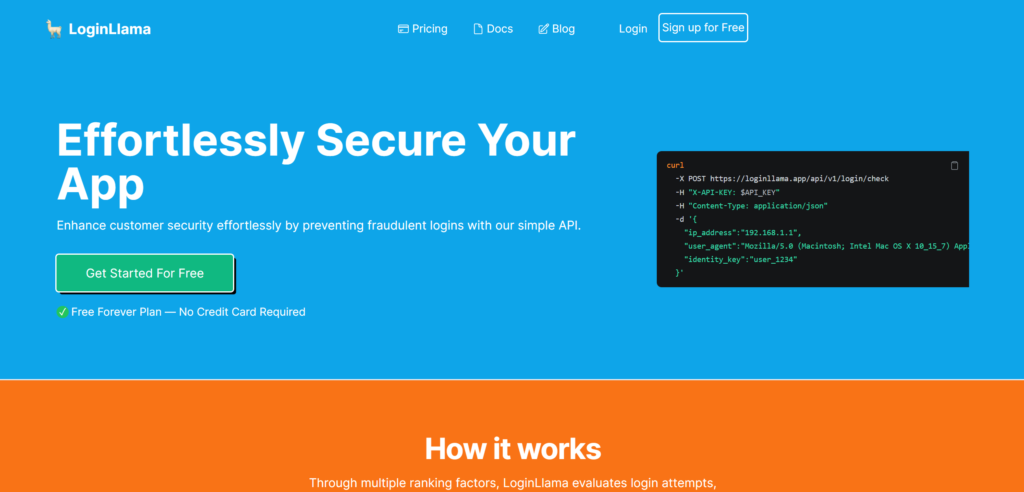
LoginLlama, the API-based guardian, offers suspicious login detection and fraud prevention for internet businesses of all sizes. This tool adds an extra layer of customer security effortlessly. Key Features: .css-8k4qb7{display:-webkit-box;display:-webkit-flex;display:-ms-flexbox;display:flex;-webkit-box-pack:start;-ms-flex-pack:start;-webkit-justify-content:flex-start;justify-content:flex-start;-webkit-align-items:center;-webkit-box-align:center;-ms-flex-align:center;align-items:center;position:relative;-webkit-text-decoration:none;text-decoration:none;width:100%;box-sizing:border-box;text-align:left;padding-top:8px;padding-bottom:8px;padding-left:16px;padding-right:16px;padding:0px;}.css-8k4qb7.Mui-focusVisible{background-color:rgba(255, 255, 255, 0.12);}.css-8k4qb7.Mui-selected{background-color:rgba(14, 165, 233, 0.16);}.css-8k4qb7.Mui-selected.Mui-focusVisible{background-color:rgba(14, 165, 233, 0.28);}.css-8k4qb7.Mui-disabled{opacity:0.38;}.css-1tsvksn{-webkit-flex:1 1 auto;-ms-flex:1 1 auto;flex:1 1 auto;min-width:0;margin-top:4px;margin-bottom:4px;}.css-yb0lig{margin:0;font-family:"Roboto","Helvetica","Arial",sans-serif;font-weight:400;font-size:1rem;line-height:1.5;letter-spacing:0.00938em;display:block;}Multi-Factor Suspicion Analysis: Utilizes historic behavior, AI analysis, request origin, and user agent to assess the level of suspicion in each login attempt.Pattern Recognition: Analyzes historic behavior to identify suspicious patterns based on time, location, and more.AI-Powered Assessment: Evaluates login attempts against the user's past behavior using AI analysis.IP Address Scrutiny: Examines IP addresses for known VPN providers or TOR exit nodes.User Agent Verification: Validates login patterns using user agent data.Comprehensive Problem Solving: Prevents unauthorized access, detects compromised accounts, blocks brute force attacks, and more.Seamless Integration: Easily integrates into existing login flows.Customizable Settings: Sensitivity controls for tailored fraud detection.Real-Time Alerts: Receive alerts for suspicious activity.Scalability: Handles high traffic loads effectively.Use Cases: Multi-Factor Suspicion Analysis: Utilizes historic behavior, AI analysis, request origin, and user agent to assess the level of suspicion in each login attempt.Pattern Recognition: Analyzes historic behavior to identify suspicious patterns based on time, location, and more.AI-Powered Assessment: Evaluates login attempts against the user's past behavior using AI analysis.IP Address Scrutiny: Examines IP addresses for known VPN providers or TOR exit nodes.User Agent Verification: Validates login patterns using user agent data.Comprehensive Problem Solving: Prevents unauthorized access, detects compromised accounts, blocks brute force attacks, and more.Seamless Integration: Easily integrates into existing login flows.Customizable Settings: Sensitivity controls for tailored fraud detection.Real-Time Alerts: Receive alerts for suspicious activity.Scalability: Handles high traffic loads effectively.Use Cases: Pattern Recognition: Analyzes historic behavior to identify suspicious patterns based on time, location, and more.AI-Powered Assessment: Evaluates login attempts against the user's past behavior using AI analysis.IP Address Scrutiny: Examines IP addresses for known VPN providers or TOR exit nodes.User Agent Verification: Validates login patterns using user agent data.Comprehensive Problem Solving: Prevents unauthorized access, detects compromised accounts, blocks brute force attacks, and more.Seamless Integration: Easily integrates into existing login flows.Customizable Settings: Sensitivity controls for tailored fraud detection.Real-Time Alerts: Receive alerts for suspicious activity.Scalability: Handles high traffic loads effectively.Use Cases: AI-Powered Assessment: Evaluates login attempts against the user's past behavior using AI analysis.IP Address Scrutiny: Examines IP addresses for known VPN providers or TOR exit nodes.User Agent Verification: Validates login patterns using user agent data.Comprehensive Problem Solving: Prevents unauthorized access, detects compromised accounts, blocks brute force attacks, and more.Seamless Integration: Easily integrates into existing login flows.Customizable Settings: Sensitivity controls for tailored fraud detection.Real-Time Alerts: Receive alerts for suspicious activity.Scalability: Handles high traffic loads effectively.Use Cases: IP Address Scrutiny: Examines IP addresses for known VPN providers or TOR exit nodes.User Agent Verification: Validates login patterns using user agent data.Comprehensive Problem Solving: Prevents unauthorized access, detects compromised accounts, blocks brute force attacks, and more.Seamless Integration: Easily integrates into existing login flows.Customizable Settings: Sensitivity controls for tailored fraud detection.Real-Time Alerts: Receive alerts for suspicious activity.Scalability: Handles high traffic loads effectively.Use Cases: User Agent Verification: Validates login patterns using user agent data.Comprehensive Problem Solving: Prevents unauthorized access, detects compromised accounts, blocks brute force attacks, and more.Seamless Integration: Easily integrates into existing login flows.Customizable Settings: Sensitivity controls for tailored fraud detection.Real-Time Alerts: Receive alerts for suspicious activity.Scalability: Handles high traffic loads effectively.Use Cases: Comprehensive Problem Solving: Prevents unauthorized access, detects compromised accounts, blocks brute force attacks, and more.Seamless Integration: Easily integrates into existing login flows.Customizable Settings: Sensitivity controls for tailored fraud detection.Real-Time Alerts: Receive alerts for suspicious activity.Scalability: Handles high traffic loads effectively.Use Cases: Seamless Integration: Easily integrates into existing login flows.Customizable Settings: Sensitivity controls for tailored fraud detection.Real-Time Alerts: Receive alerts for suspicious activity.Scalability: Handles high traffic loads effectively.Use Cases: Customizable Settings: Sensitivity controls for tailored fraud detection.Real-Time Alerts: Receive alerts for suspicious activity.Scalability: Handles high traffic loads effectively.Use Cases: Real-Time Alerts: Receive alerts for suspicious activity.Scalability: Handles high traffic loads effectively.Use Cases: Scalability: Handles high traffic loads effectively.Use Cases: Use Cases: Enhanced Security: Safeguard customer accounts with multi-factor suspicion analysis.Fraud Prevention: Prevent unauthorized access and protect against various login threats.User-Friendly Integration: Easily integrate into existing login systems. Fraud Prevention: Prevent unauthorized access and protect against various login threats.User-Friendly Integration: Easily integrate into existing login systems. User-Friendly Integration: Easily integrate into existing login systems. Why Use LoginLlama: LoginLlama offers comprehensive suspicious login detection and fraud prevention with easy integration, customizable settings, real-time alerts, and scalability. Choose from flexible pricing plans, including a free option, and benefit from reliable support and privacy-focused policies. Elevate your security with LoginLlama's seamless protection.
Product Video
Categories
Links
Promote
Customer Reviews
Review
Write a ReviewThere are no reviews yet.
Leave a Review
Similar AI Tools
Popular Tabnine
0.0 0 reviewsPopular MutableAI
0.0 0 reviewsPopular Mintlify
0.0 0 reviews





